BleepingComputer Review:
Norton AntiVirus is a powerful application designed to protect your Mac against viruses, malware and network vulnerabilities that would allow others to access your system. Scans for and blocks.
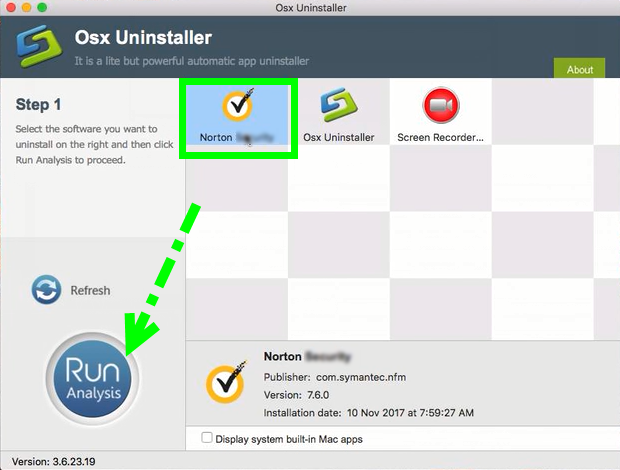
The Norton Anti-Virus Removal Tool will allow you to remove a damaged installation of a Norton or Symantec product that will not uninstall properly through the Windows control panel. In the event that Norton becomes damaged by a bad install or due to a virus, it makes it difficult, if not impossible, to uninstall it normally. In situations like this you can use the Norton Removal Tool to scan your computer for all Norton products and completely remove them.
It should be noted that this tool will not prompt you for the products that you wish to uninstall. Therefore, make sure you have all data backed up for your Norton programs before proceeding.
This program will remove the following Norton Products:
- Norton™ provides industry-leading antivirus and security software for your PC, Mac, and mobile devices. Download a Norton™ 360 plan - protect your devices against viruses, ransomware, malware and other online threats.
- Use the Norton Removal Tool to remove a failed installation or a damaged Norton product. The Norton Removal Tool uninstalls all Norton Antivirus products, Norton 360 and Norton SystemWorks from your computer. Or WinFAX, back up those databases before you proceed. Norton Remove and Reinstall Tool 4.5.0.148 on 32-bit and 64-bit PCs.
- On the menu bar, click Go Applications. Do one of the following: If an app isn't in a folder or doesn't have an Uninstaller, drag the app from the Applications folder to the Trash, then choose Finder Empty Trash. If the app is in a folder, open the app's folder to check for an Uninstaller.
- Norton AntiSpam 2004 and 2005
- Norton AntiVirus 2003-2012
- Norton Ghost 2003, 9.0, 10.0, 12.0, 14.0, and 15.0
- Norton GoBack 3.1 through 4.2
- Norton Internet Security 2003 through 2012
- Norton Password Manager
- Norton Personal Firewall 2003 through 2006
- Norton SystemWorks 2003 through 2009
- Norton Confidential Online 2007
- Norton Add-on Pack 1.0 - 4.0
- Norton Save and Restore 1.0 and 2.0
- Norton 360/Security Suite/Business Suite 1.0 - 6.0
- Norton Saftey Minder 1.0
- Norton SafeWeb 3.2
Company's Description:
The Norton Removal Tool uninstalls all Norton 2003 and later products, Norton 360, and Norton SystemWorks 12.0 from your computer. Before you continue, make sure that you have the installation CDs or downloaded installation files for any Norton products that you want to reinstall. If you have pcAnywhere or WinFAX, uninstall it using Add or Remove Programs before running the Norton Removal Tool. Also, if you use ACT! or WinFAX, back up those databases and uninstall those products.
Oct. 1, 2020
It’s possible to remove malware from a Mac or PC by running a scanner and taking steps to fix your web browser. Here’s our step-by-step guide to removing malware from your computer.
How to remove malware from a Mac
Step 1: Disconnect from the internet
Disconnecting from the internet will prevent more of your data from being sent to a malware server or the malware from spreading further. So stay offline as much as possible if you suspect that your computer has been infected. If you need to download a removal tool, disconnect after the download is complete and don’t connect again until you are sure that the malware has been removed.
Step 2: Enter safe mode
Safe mode, often referred to as safe boot, is a way to start your computer so that it performs checks and allows only the minimum required software and programs to load. If malware is set to load automatically, this will prevent the malware from doing so, making it easier to remove. To enter safe mode:
- Start (or restart) your Mac, then immediately press and hold the Shift key. The Apple logo will appear on your display.
- Release the Shift key when you see the login window (if you are asked to log in twice, learn more about what to do here).
Disclaimer: Avoid logging into accounts during malware removal
Be careful to not expose passwords though a copy-paste function or by clicking a ‘show password’ box if you suspect your computer has been infected. Keylogger viruses are a common component of malware, which run invisibly and are designed to capture your keystrokes. To avoid sharing your personally identifiable information, refrain from logging into sensitive accounts while your device is infected.
Step 3: Check your activity monitor for malicious applications
If you know that you’ve installed a suspicious update or application, close the application if it’s running. You can do so by using your activity monitor. This shows the processes that are running on your computer, so you can manage them and see how they affect your computer’s activity and performance.
Malware can take up resources on your computer, so check the CPU tab to see which applications are working the hardest. If you are able to find the suspicious application, you can close out of it through your activity monitor and then delete the application from the Finder menu. To check your activity monitor:
In Finder, click → Applications → Utilities → Activity Monitor → Select Application → Quit
Step 4: Run a malware scanner
Fortunately, malware scanners can remove most standard infections. It’s important to keep in mind that if you already have an antivirus program active on your computer, you should use a different scanner for this malware check since your current antivirus software may not detect the malware initially. If you believe your computer is infected, we recommend downloading an on-demand scanner from a reliable source and then installing and running security software which provides protection against existing and emerging malware, including ransomware and viruses.
Step 5: Verify your browser’s homepage

It’s common for malware to modify your web browser’s homepage to re-infect your Mac. Check your homepage and connection settings using the steps below for common browsers. Note that you will need to connect your computer to the internet to complete the following steps.
To verify your homepage on Chrome:
- In the top right corner of your Chrome browser, click More → Settings.
- Select the dropdown menu in the “Search engine” section.
- Verify your default homepage.
To verify your homepage on Safari:
- In the top left corner of your screen, select Safari → Preferences → General.
- Next to “New windows open with” and “New tabs open with,” select Homepage.
- Next to “Homepage,” you will verify your default homepage.
Step 6: Clear your cache
After you’ve verified your homepage setting, you should clear your browser’s cache. This is a temporary storage location on your computer where data is saved so your browser doesn’t need to download it each time. Follow these steps below to learn how to clear your cache for Chrome and Safari.
To clear your cache on Chrome:
Select Chrome → History → Clear Browsing Data → Time Range → All Time → Clear Data.
To clear your cache on Safari:
Select Safari → Preferences → Privacy → Manage Website Data → Remove All.
How to remove malware from a PC
Step 1: Disconnect from the internet
Disconnecting from the internet will prevent more of your data from being sent to a malware server or the malware from spreading further.
Step 2: Enter safe mode
If malware is set to load automatically, this will prevent the malware from loading, making it easier to remove. To enter safe mode:
- Restart your PC.
- When you see the sign-in screen, hold down the Shift key and select Power → Restart.
- After your PC restarts, to the “Choose an option” screen, select: Troubleshoot → Advanced Options → Startup Settings.
- On the next window, click the Restart button and wait for the next screen to appear.
- A menu will appear with numbered startup options. Select number 4 or F4 to start your PC in Safe Mode.
Disclaimer: Avoid logging into accounts during malware removal
To avoid sharing your personally identifiable information, do not log into sensitive accounts while your device is infected.
Step 3: Check your activity monitor for malicious applications
If you know that you’ve installed a suspicious update or application, close the application if it’s running. Your activity monitor shows the processes that are running on your computer, so you can see how they affect your computer’s activity and performance.
In Type to search type → Resource Monitor → Find End Task → Right Click → End Process
Step 4: Run a malware scanner
Luckily, malware scanners can remove many standard infections. But remember that if you already have an antivirus program active on your computer, you should use a different scanner for this malware check since your current antivirus software may not detect the malware initially.
Step 5: Fix your web browser
Malware is likely to modify your web browser’s homepage to re-infect your PC. Check your homepage and connection settings using the steps below for common browsers.
To verify your homepage on Chrome:
4. In the top right corner of your Chrome browser, click More → Settings.
5. Select the dropdown menu in the “Search engine” section.
6. Verify your default homepage.
To verify your homepage on Internet Explorer:
- Select the Tools icon.
- Click Internet options.
- In the General tab, find the “Search” section and click Settings.
- Verify your default homepage.
Step 6: Clear your cache
After you’ve verified your homepage setting, it’s imperative to clear your browser’s cache. Follow these steps below to learn how to clear your cache for Chrome and Internet Explorer.
To clear your cache on Chrome:
History → Clear Browsing Data → Time Range → All Time → Clear Data.
Norton Removal Tool Software For Mac Windows 10
To clear your cache on Internet Explorer:
Tools → Safety → Delete browsing history.
What if malware removal is unsuccessful?
If malware removal is unsuccessful, sometimes the only way to be sure your computer is free of malware is to entirely reinstall the operating system and your applications or programs from scratch. Before wiping your hard drive, backup all your files to an external drive and consult Apple support or Microsoft support before beginning the process. Learn how to erase your startup disk prior to reinstalling MacOS in the steps below:
To reinstall MacOS:
Restart the Mac and hold down Command-R after the startup chime sounds → Select Disk Utility → Erase.
To reinstall Windows:
Follow the factory restore options. Windows gives you the option to keep your files or remove everything.
Select the Start button → Settings → Type Recovery Options → Reset this PC → Get started → Remove everything
How to tell if your device has been infected with malware

Some of the tell-tale signs of your device being infected with malware include:
- Changes in your device behavior: for example, unusual ads or pop-up windows may begin to appear, even when you’re not surfing the web.
- Your device may begin to run more slowly.
- Your device may suddenly lack storage space.
- Your browser behavior or homepage appearance may change.
- Ads may pop up featuring inappropriate content and flashing colors. They may also block whatever content you’re trying to view.
How to help protect your devices from malware
Malware or viruses get on your computer in a handful of ways, so it’s a good idea for computer owners to develop good online habits to avoid an infection. Use our best practices below to help protect your computer:
- Avoid suspicious emails, links, and websites. Sometimes malware or viruses are disguised as an image file, word processing document, or PDF that you open. Additionally, if you find a strange new file on your desktop, do not open it.
- Clear your downloads and empty your trash often. If you’ve deleted downloads or moved suspicious files to the trash, empty the trash immediately after.
- Create strong passwords. Once you’re sure the computer virus infection has been cleaned up, change all your passwords, using unique combinations of letters, numbers, and symbols. Don’t use words found in the dictionary since they can be cracked via a dictionary attack. To help create, manage, and securely store all your passwords, consider using a password manager.
Malware is a dangerous threat to the data that computer owners store on their PCs and Macs. New types of malware are being discovered frequently, and the profitable nature of some types of malware can make it especially attractive to cybercriminals around the globe. It’s important to exercise good online habits and understand the signs of a malware infection.
Norton Software Removal Tool Mac
If you suspect your computer is infected, act as soon as possible to prevent the spread of malware and protect your personal information.
Try Norton 360 FREE 30-Day Trial* - Includes Norton Secure VPN
Norton Removal Tool Software For Mac Download
30 days of FREE* comprehensive antivirus, device security and online privacy with Norton Secure VPN.
Norton Removal Tool Software For Mac Osx
*Terms Apply
Norton Removal Tool Software For Mac Os
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.
